Cyberattacks hit businesses every day. John Chambers, CEO of the multinational Cisco said: "There are two types of companies: those that have been hacked and those that have been hacked but do not know it. To combat a world where computer security has become one of the pillars of organizations, in this article we explain the different types of cybersecurity attacks and what they consist of. Keep reading!
Types of Cybersecurity Attacks: What is a Cyber Attack?
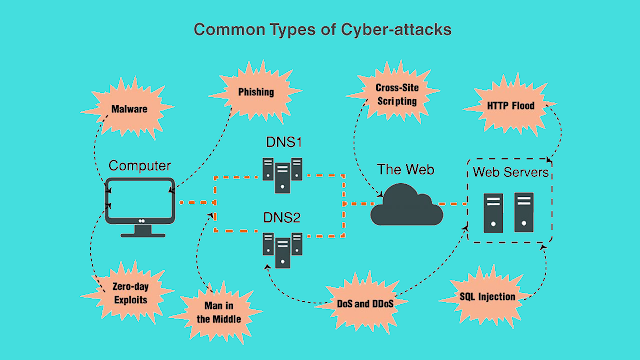
For starters, what is a cyber attack? A cyber attack is a set of offensive actions against information systems. These can be databases, computer networks, etc. The objective is to damage, alter, or destroy organizations or people. In addition, they can take down the services they provide, steal data, or use it to spy.
We live in a digital age. Today most people use a computer with the Internet. Therefore, due to the dependence on digital tools, illegal computer activity grows without stopping and seeks new and more effective forms of crime.
We can classify the types of cybersecurity attacks into three categories:
- Phishing attacks
- Malware attacks
- Web attacks
PHISHING
Phishing is a type of social engineering that is used, generally, to steal user data. They can be credit card numbers or passwords, for example. It occurs when a criminal poses as a trusted person. Then it tricks the victim into opening a text, email, or SMS message using a malicious link. This link can cause a ransomware system to freeze, reveal confidential information, or install malware.
It is simple and very easy to use the technique, which is why it is one of the most dangerous. It can have disastrous results. For an individual, it can lead to identity theft, funds theft, or unauthorized purchases.
SPEAR PHISHING
On the other hand, spear phishing is computer attacks that target a specific person or employee of a specific company. To carry out these types of attacks, criminals meticulously collect information about the victim to gain their trust. Falling for these attacks is usually very common, since a well-prepared email, either with a malicious link or attachment, is very difficult to distinguish from a legitimate one.
This technique is widely used to attack companies, banks, or influencers.
WHALING
In third place on the list of types of cybersecurity attacks, we find whaling attacks. These attacks target a senior manager profile, such as CEOs or CFOs. The objective, like the previous ones, is to steal vital information, since those who occupy high positions in a company usually have unlimited access to confidential information. In most of these so-called "whaling" scams, the offender manipulates the victim to allow high-value wire transfers.
The phrase "whaling" refers to the size of the attack, as the whales are attacked depending on their position within the organization. These types of attacks are easier to detect compared to standard phishing. A company's IT security officers can reduce the effectiveness of this hack.
Malware or Malicious Software
Second, among the types of cybersecurity attacks are malware. Malware is code created to stealthily corrupt a computer system. It is a broad term that describes any malicious program or code that is harmful to systems. Intrusive malware invades, damages, or disables computers, computer systems, mobiles, etc. assuming control of operations.
The goal of malware is usually to get money from the user illegally. Although it generally cannot damage the hardware of the systems, it can steal, encrypt, erase data, or hijack the basic functions of a computer, as well as spy on its activity without anyone noticing.
Malware includes many types of malicious software, such as spyware, ransomware, Trojans, etc.
RANSOMWARE OR DATA HIJACKING
Ransomware is malicious software that, by penetrating our computer, gives the hacker the ability to block a device from a remote location. Also to encrypt the files, removing the user control of all the information and data stored.
In terms of its method of spread, ransomware is usually transmitted as a Trojan. That is, infecting the operating system. For example, downloading a file or exploiting a software vulnerability. The cybercriminal, who has encrypted the operating system files rendering the device unusable, usually asks for a ransom in exchange for removing the restriction on the documents.
AUTOMATIC DOWNLOADS
Automatic downloads to spread malware are one of the most common methods among types of cybersecurity attacks. Cybercriminals search for insecure web pages and plant a malicious script in the HTTP or PHP code on one of them. This script can install malware directly on the device of the user visiting the site. It can also take the form of an iframe that redirects the victim to a site controlled by the attackers. These attacks are called "automatic downloads" because they require no action on the part of the victim. You just have to visit that website.
TROJAN
A Trojan is a malicious software program that tries to disguise itself as a useful tool. They apparently spread software and persuade a victim to install it. Trojans are considered among the most dangerous types of cybersecurity attacks, often designed to steal financial information.
Users are tricked by some form of social engineering into loading and running Trojans on their systems. U activated nice, they allow cybercriminals to spy or steal your confidential information. Unlike viruses and worms, Trojans cannot replicate themselves.
For malware to be a Trojan, it only has to access and control the host machine without warning, under an innocuous appearance.
Attacks on a website
SQL INJECTION
Among the most popular types of cybersecurity attacks is SQL Injection. It is a method of infiltration of an intruder code that takes advantage of a computer vulnerability present in an application. That is, they take advantage of common design errors on web pages. The threat of SQL injections is a serious security problem related to databases. They are used to manipulate, steal, or destroy data.
Cybercriminals are capable of injecting malicious SQL queries into a website's input field, tricking the application into using the commands they want, and accessing the database they want.
An SQL injection attack can slow down the operation of a website, theft, loss or corruption of data, denial of access by any company, or even take full control of the server.
XSS OR CROSS SITE SCRIPTING
XSS attacks use third-party web resources to run scripts in the victim's web browser or programmable application.
They are a kind of injection in which the attacker sends malicious scripts to the content of web pages to discredit them. This occurs when a dubious source can attach its own code in web applications. This is sent in the form of Javascript code snippets executed by the victim's browser.
Exploits can include malicious executable scripts in many languages, including Flash, HTML, Java, and Ajax. XSS attacks can be very devastating. However, alleviating the vulnerabilities that these attacks allow is relatively simple.
What did you think of this article about the types of cybersecurity attacks? Leave us your comments and share! Also, do not forget to install total security software to protect your data from cybersecurity attacks.




No comments:
Post a Comment