One of the strongest sales campaigns in shops and online sales recently established in Spain is Black Friday and Cyber Monday. A tradition imported from the US where all physical stores and online businesses make numerous discounts on all their products for the Christmas season.
It is a good time to catch a bargain ... If you are thinking of doing it in an online store, you should take into account a series of tips to avoid possible upsets and make your purchases 100% safely:
1. Activate a Card for Online Payments and Deactivate It When You Have Finished Your Purchases 💳
For the maximum security of your bank accounts, many entities enable free virtual cards to be able to make purchases online safely. We will activate and deactivate these cards only when we are going to make a purchase online.
2. Buy on Websites With Trusted Seals 📝
Cybercriminals can spoof websites to mislead consumers into believing that they are buying from a legitimate site. The website may appear almost identical to the real site; however, subtle changes may indicate that it is not. Take a good look at the URLs.
If you are visiting an e-commerce website for the first time, look to see if it has a trust seal such as Confianza Online or Trusted Shops. These seals guarantee that member companies are periodically subjected to complete quality, safety, and service evaluation.
3. Only Use Secure Sites With Certificates 🔒
The way to know if a web page has HTTPS is by looking at the browser. When accessing any website, you can see an indicator in the upper left part of the browser that indicates whether or not the page uses the HTTPS protocol. Depending on the browser, it will be seen in a different way but in all of them, it will be very clear if the web is secure or not. Certified web pages display a lock next to the domain. When you click on the padlock, a message appears indicating that the connection is made safely.
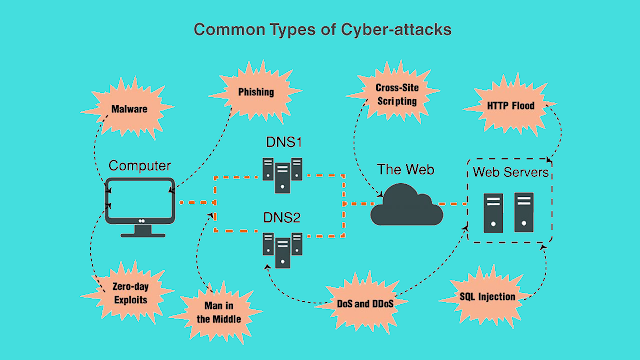
4. Be Wary of Suspicious Bargains 🏷
On “Black Friday” and “Cyber Monday” many cybercriminals take advantage of it by replicating and introducing many fake offers.
It can be difficult to tell the difference between a real offer and a fake, so it is best to make sure that a website is real. Shop at reputable and trustworthy stores that you know or have recommended to you. Avoid eCommerce that are unknown or that offer dubious discounts that are hard to believe.
5. Find Out About the Ecommerce Where You Are Going to Buy 🔍
Check that the seller's contact information appears on the website and that the conditions of use are clearly explained: shipping costs, return policy, customer service ... If you have questions, try to contact them before making a buy or consult their social networks to read opinions of other users.
6. Be Careful With the Wifi Networks We Connect to 📶
Many public spaces such as cafeterias or train stations have free access to WIFI networks. What we must ask ourselves is: Are they safe? Many cybercriminals simulate free Wi-Fi networks in order to access our devices. When in doubt, use your mobile's own internet.
9. Use Strong Passwords 🔐
It's always best to use a unique username and password for your various accounts, so in the unfortunate event of being the victim of an attack, cybercriminals won't have access to all of your accounts.
10. Beware of Fraudulent Emails or Phishing 📧
Phishing is a technique frequently used by hackers, with which forged emails are sent, with an aesthetic appearance very similar to the original, whose mission is to manipulate the user who receives it to steal confidential information.
You Can Identify a Phishing Email in Our Post.
Checking typographical errors, installing antivirus software on our computer, not sharing bank details by email or messaging, are other aspects to take into account when making your purchases online. Enjoy this Black Friday and Cyber Monday in a 100% safe way! 🛍🛒